Picture this scenario: it’s way past lunchtime, and you’ve been in Human Resources meetings all morning.
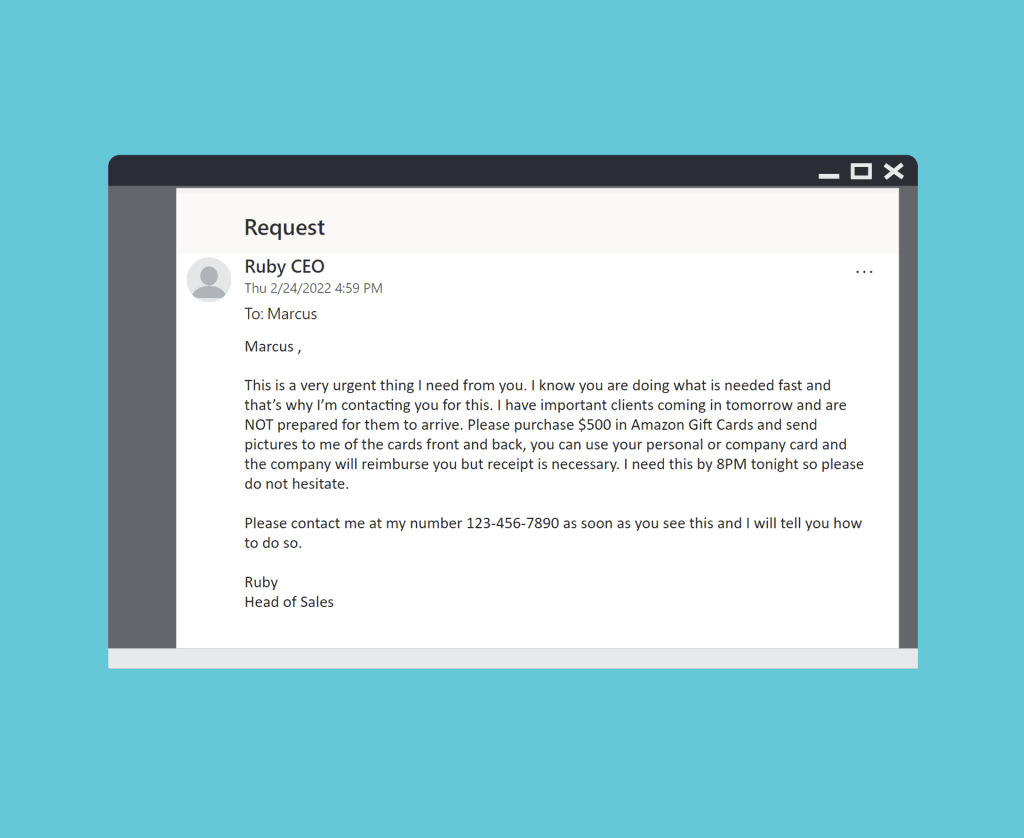
Stomach grumbling, you take a quick look at your email before finally going on lunch. That’s when you see an alarming email from the Human Resources Vice President with the subject line, “URGENT! PLEASE RESPOND ASAP!”
Your heart immediately starts pounding. In the email, your VP explains that they’ve changed banks and need you to update their direct deposit information in the company payroll system. They provide you with the new banking details and ask you to respond when you’re done.
What do you do next?

Your response largely depends on whether you understand the psychology behind phishing techniques like the one used in that email.
When your team understands the social engineering behind phishing techniques (and adopts mindfulness practices that can alert them to such tactics), your organization will have a more formidable defense against would-be data thieves.
Organizations pour money and time into cybersecurity initiatives, but these measures often fail because they do not address the human factors that enable cybercrimes like phishing.
The truth is that cybercriminals’ best weapon isn’t malware, faulty security, or weak passwords; it’s people.
Traditional cybersecurity training tends to focus on the technical aspects of cybercrime:
- how it happens
- what to look for
- and how to stop it from happening
While preventative best practices and an understanding of red flags will help your team stop data breaches, these measures don’t address the in-the-moment actions and decisions that are critical to protecting your organization’s data.
When your team understands the social engineering behind phishing techniques (and adopts mindfulness practices that can alert them to such tactics) your organization will have a more formidable defense against would-be data thieves.
The social engineering framework cybercriminals use to steal your information
What is the psychology that makes cybercrimes like phishing possible?
In his book Influence: The Psychology of Persuasion, behavioral psychologist Robert Cialdini provides a framework for understanding how social engineering and human biases can manipulate behavior. This framework sheds light on the strategies that cybercriminals use to trick typically vigilant employees.
Let’s take a look at how cybercriminals use our own brains to gain access to our data.
Pretexting
Pretexting is masquerading as someone else — generally, pretending to be a person the victim knows or would expect to hear from.
This could be in the form of a text or email that appears to be from:
- your boss
- a colleague
- a relative
- a known institution, such as your bank or FedEx
- a government agency, like the IRS (Internal Revenue Services)
When you receive this phishing communication, your brain tends to automatically assume that it’s real, leading you to jump into the content of the message and respond to its directions quickly, rather than to examine whether the sender is authentic.
Authority Influence
Authority influence is extremely effective because we tend to obey authority figures, even when are asked to perform questionable or even objectionable acts.
For this reason, cybercriminals often pretext as an authority figure — usually an employee’s manager or boss, or personnel from an authority institution — to induce an employee to click on a link or provide sensitive information. To the unmindful brain, the urge to obey authority may override concerns about information security.

For example, in this story about her work as a “people hacker,” Jenny Radcliffe of Human Factor Security describes how she got past a security system that cost 2 million pounds with a single piece of paper, which was a note saying “Please do not close this door. Thank you. – HR.”
Thankfully, the company was a client of Radcliffe’s. She had broken into the building as part of a planned security test, so nothing was stolen. However, the security team was (reasonably) quite shaken.
The unquestioning obedience to authority the company had nurtured in their culture was a huge liability. A criminal need only invoke the voice of an authoritative figure and employees would break protocol, exposing the company to risk.
Scarcity or Urgency
In his second book on persuasion, Influence: Science and Practice, Robert Cialdini coined the scarcity principle: “people are more likely to assign higher value to opportunities that appear to be less available.”
You probably encounter this concept regularly. This principle is at play when you pass a shop window displaying signage saying, “40% off, TODAY ONLY!” or when an online marketplace announces, “5 left in stock. Currently in 8 shopper’s carts.” Creating a sense of urgency heightens the sense of importance and compels us to respond in the moment – whether that means buying new shoes or inadvertently sharing secure data.
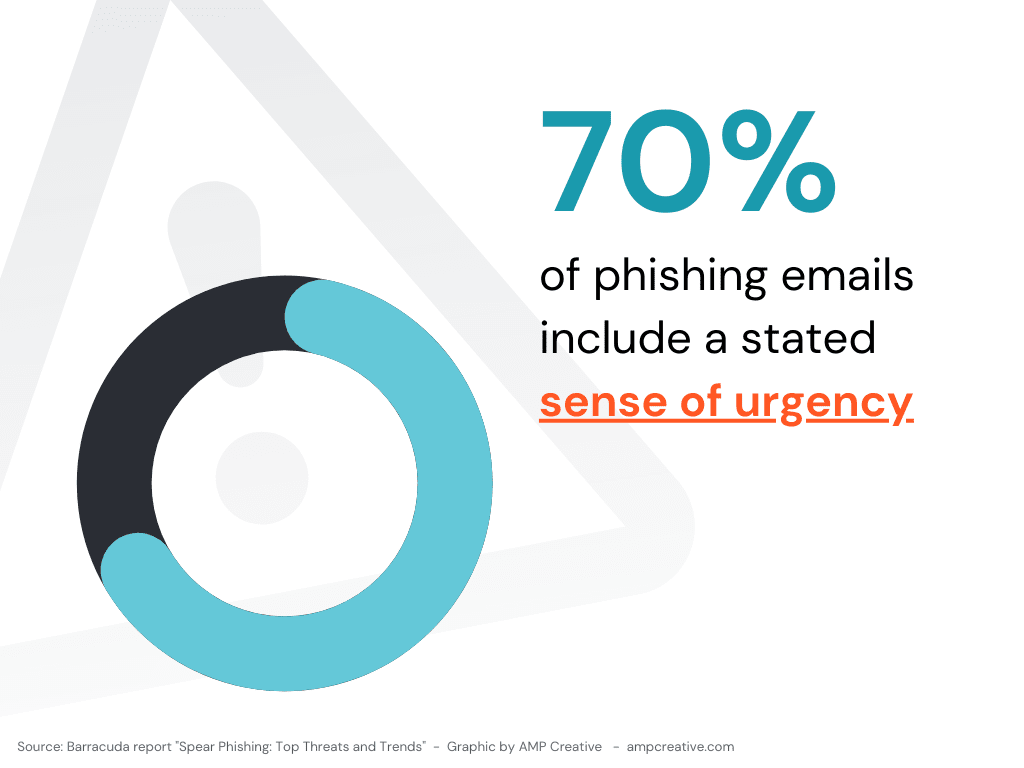
According to a report by the security firm Barracuda Networks, 70% of phishing emails studied included a stated sense of urgency. This technique can cause the email recipient to feel flustered or stressed, which may lead them to skip steps or act too quickly in order to fulfill what is perceived as an order from an authority.
The phishing attack
Cybercriminals often employ all three of these persuasion techniques at once.
Via pretexting, they may pretend to be an authority figure and urge targets to act fast, think later. This can compel employees to hand over data that, in another context, they would have guarded carefully.
Upon closer examination, phishing attempts can be easy to recognize. So why do these techniques work?
The Limbic System & Amygdala Hijacking
To better understand why these persuasion techniques work, we have to understand the way different parts of the human brain function – in this case, the limbic system.
The limbic system is the part of the brain that governs behavioral and emotional reactions; it’s the home of the fight/flight/freeze response. It has no capacity for language and processes information much faster than the cognitive brain.
That means if a cybercriminal is trying to persuade someone to download malware or hand over sensitive information, they will appeal to that person’s emotions – their limbic system – rather than their high-functioning critical-thinking system, which is much better at assessing risk.
Risk-assessment skills originate in the prefrontal cortex, the site of executive functioning. There, brain processing is slower, non-reactive, and much more careful to evaluate the situation. The prefrontal cortex is what cybercriminals seek to override, so they can kick the emotional part of our brains into reactive high gear.
In his book Emotional Intelligence: Why It Can Matter More Than IQ, Daniel Goleman describes situations in which stress and social cues can hijack our brains.
In these situations, our careful prefrontal cortex isn’t in control. What’s at the wheel? Our reactive, impulsive limbic system.
In this role reversal, it’s the amygdala – the part of the limbic system that produces stress hormones like adrenaline and cortisol – that’s in charge of decision-making. Our focus narrows down, our critical thinking becomes limited, and our ability to consider the perspectives of others takes a nosedive. Reactionary hormones surge through the body and enable us to take rapid action – the so-called “amygdala hijack.”
This is a great response when you need to flee a charging grizzly bear. It’s less effective for identifying when a cybercriminal is trying to access your work computer.
Using mindfulness to resist phishing techniques
So, back to that frantic email from your Human Resources Vice President. How did you react? Even if you were trained in traditional cybersecurity protection, it’s all too likely you fell for the phishing scam.
You wouldn’t be alone! More than 25% of American workers fall for these scams.
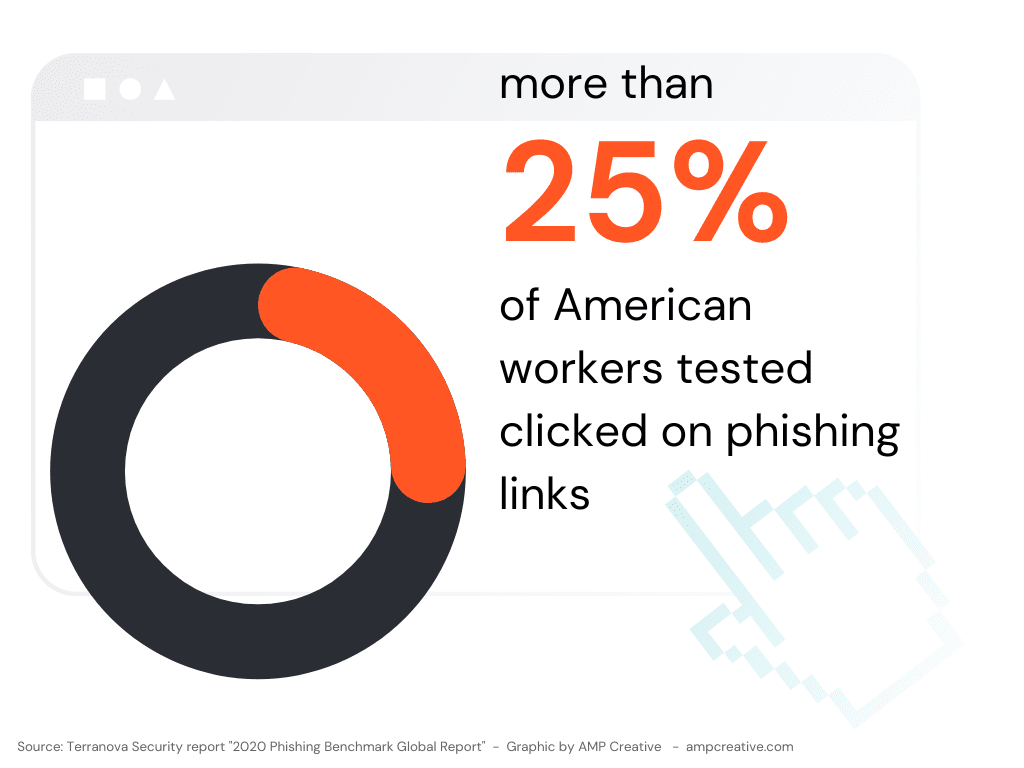
Why? Traditional cybersecurity training teaches employees to look for signs of fraud. But it doesn’t teach them to listen to their bodies.
When the limbic system is stimulated, we feel it. Our heart rate goes up. We get sweaty, dry-mouthed, thick-headed, and anxious.
The STOP method for mindfully combatting psychological pressure
When we are feeling symptoms associated with anxiety, fear, and urgency, we need to STOP.
This method, developed by Jon Kabat-Zinn for his course “Mindfulness-Based Stress Reduction,” is a simple way to halt panic in its tracks.
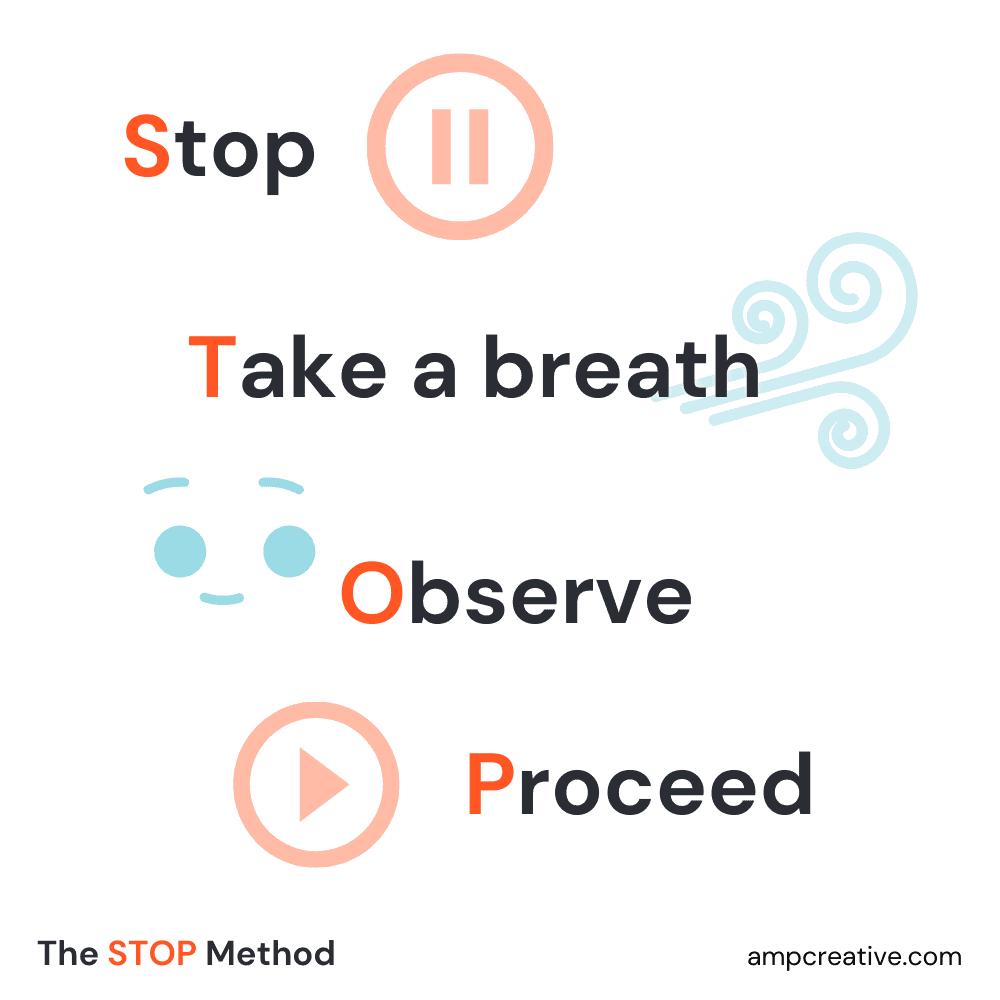
S: Stop
Stop what you’re doing; set down your current task and allow yourself to mentally take a break from it.
T: Take a breath
Breathe in deeply and just focus on your breath.
O: Observe
Observe what you feel and what is happening around you.
P: Proceed
Now that you’ve taken a moment to reset, return to the task.
How this mindfulness technique protects you from phishing
Taking this time to stop and breathe begins to engage the prefrontal cortex.

When we take a couple of deep breaths in and out, we are calming our limbic brains. We’re taking the reins back from the amygdala, reminding ourselves there’s no large animal coming to eat us, and beginning to access our complex problem-solving abilities again.
After stepping away from that initial emotional reaction, we can better to decide what to do. We can consider: does Xuan, the HR VP, usually send out big announcements with this many typos? Don’t we usually handle payment info through a company portal? When was the last time such a big systems change happened so quickly – and without any notice?
When we can calmly consider the facts, it’s much easier to tell something is amiss.
This is a simple mindfulness meditation practice: take a deep breath in and out before responding to urgent or sensitive messages. However, it’s also a powerful tool, giving us a better chance of recognizing (and thwarting) phishing attempts.
Cybercriminals are just humans with an understanding of the human mind and its weaknesses. With a better understanding of our own minds through mindfulness training, we can create a human firewall ready to withstand even the most aggressive attacks.
Mindfulness and the workplace
Growing awareness of mindfulness practices is changing company cultures across America for the better. Give the STOP method a try, but don’t stop there. Implementing mindfulness practices can help your team in many ways. They can lower stress levels, help prevent burnout, and keep your team compassionate through conflict.
Interested in strengthening your team with mindfulness training? Reach out to AMP today to learn more.
Featured image by Ekrulila.